InsightIDR
Tags:
Insight IDR is a cloud-native security solution that empowers teams to detect, investigate, and respond to threats with speed and precision. It unifies advanced analytics, automation, and real-time intelligence in a single platform. In addition to its core threat detection capabilities, Insight IDR offers User and Attacker Behavior Analytics, visual incident timelines, endpoint interrogation, and automated containment actions.
Choose Quantity
$100.00
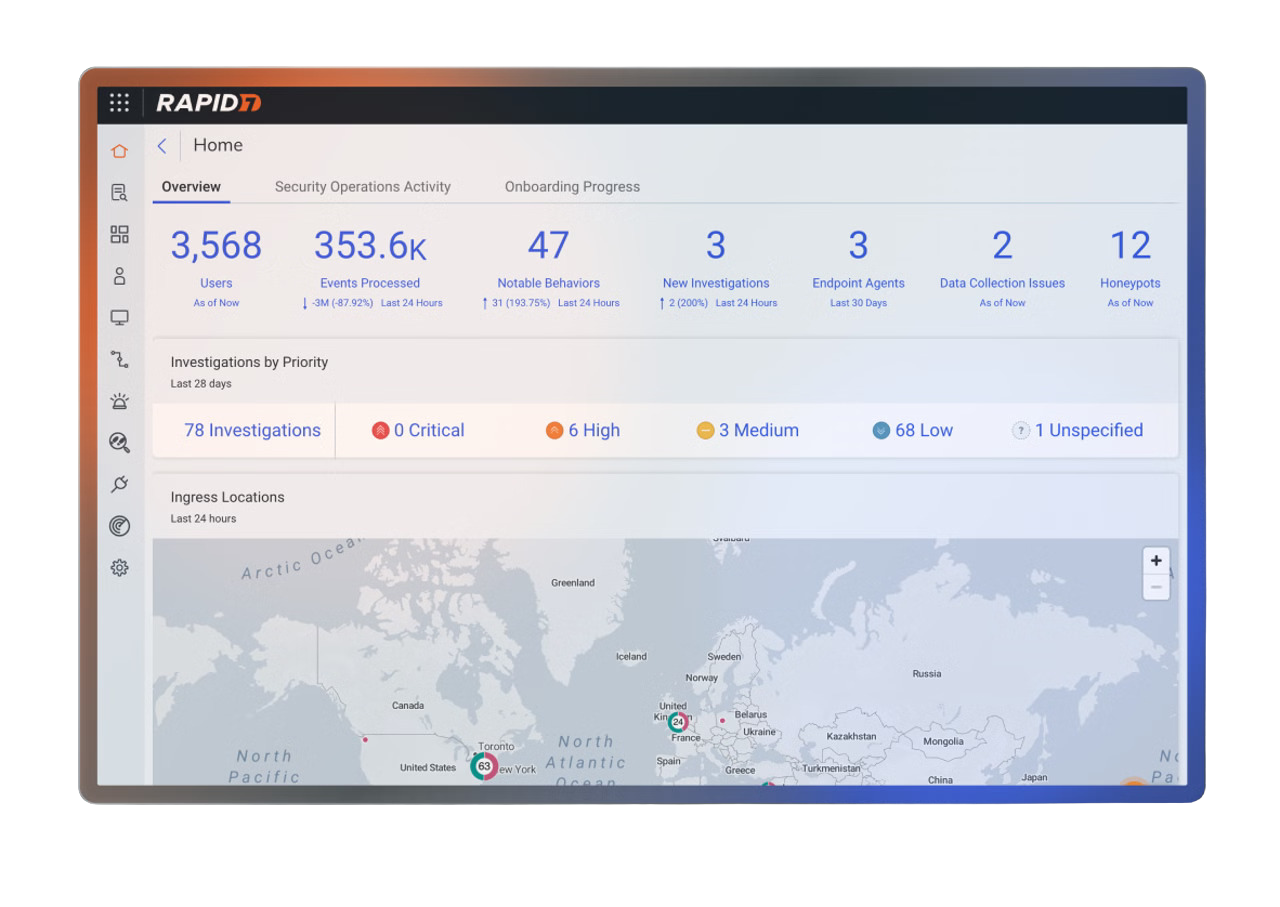
Product Details
Extended Detection and Response (XDR)
- Reliable endpoint threat detection through a detections-first approach powered by the Insight Agent
Network Traffic Analysis (NTA)
- The Insight platform’s Network Sensor unlocks critical network visibility and detection coverage, alongside data from the rest of your environment. With the lightweight sensor in place, you can quickly recognize suspicious activity on the network.
User and Entity Behavior Analytics (UEBA)
- Continuously baselines normal user activity (beyond defined indicators of compromise). Attackers may be masked as company employees, but it’s no match for UEBA. Correlated user data also offers up rich context for other attacker alerts to help speed your investigations and response.
Cloud and Integrations
- Built for dynamic, ever-changing environments to keep you a step ahead of even the slickest attackers. You can spot anomalous activity or threats in the cloud easily. And you can pull in detections from other systems to analyze and investigate them alongside the rest of your data.
Embedded Threat Intelligence
- Integrates curated threat intelligence from Vulnerability Guard’s community, proprietary machine learning, and expert teams. Delivered via SaaS, it ensures up-to-date detections without manual rule tuning—giving you instant, reliable insights across your attack surface.
MITRE ATT&CK alignment
- Vulnerability Guard’s vast library of curated detections and attacker behaviors is mapped in detail to the MITRE ATT&CK® framework, an open, globally-accessible knowledge base of real-world adversary tactics and techniques.
Deception Technology
- Built-in deception suite deploys honeypots, honey users, credentials, and files to expose attackers early. By expanding detection beyond endpoints, it traps malicious behavior before it escalates—no complex setup required.
Incident Response and Investigations
- Streamlines investigations by auto-enriching alerts with user and asset context, correlating events across sources, and generating visual timelines. No tab-hopping—just clear, actionable insights when you need them most.
Response and Automation
- Reduces manual work with prebuilt workflows for threat containment, user suspension, and ticketing integration. With InsightConnect, teams can trigger response playbooks instantly—backed by expert recommendations for every alert.
