Digital Risk Protection
Digital Digital Risk Protection
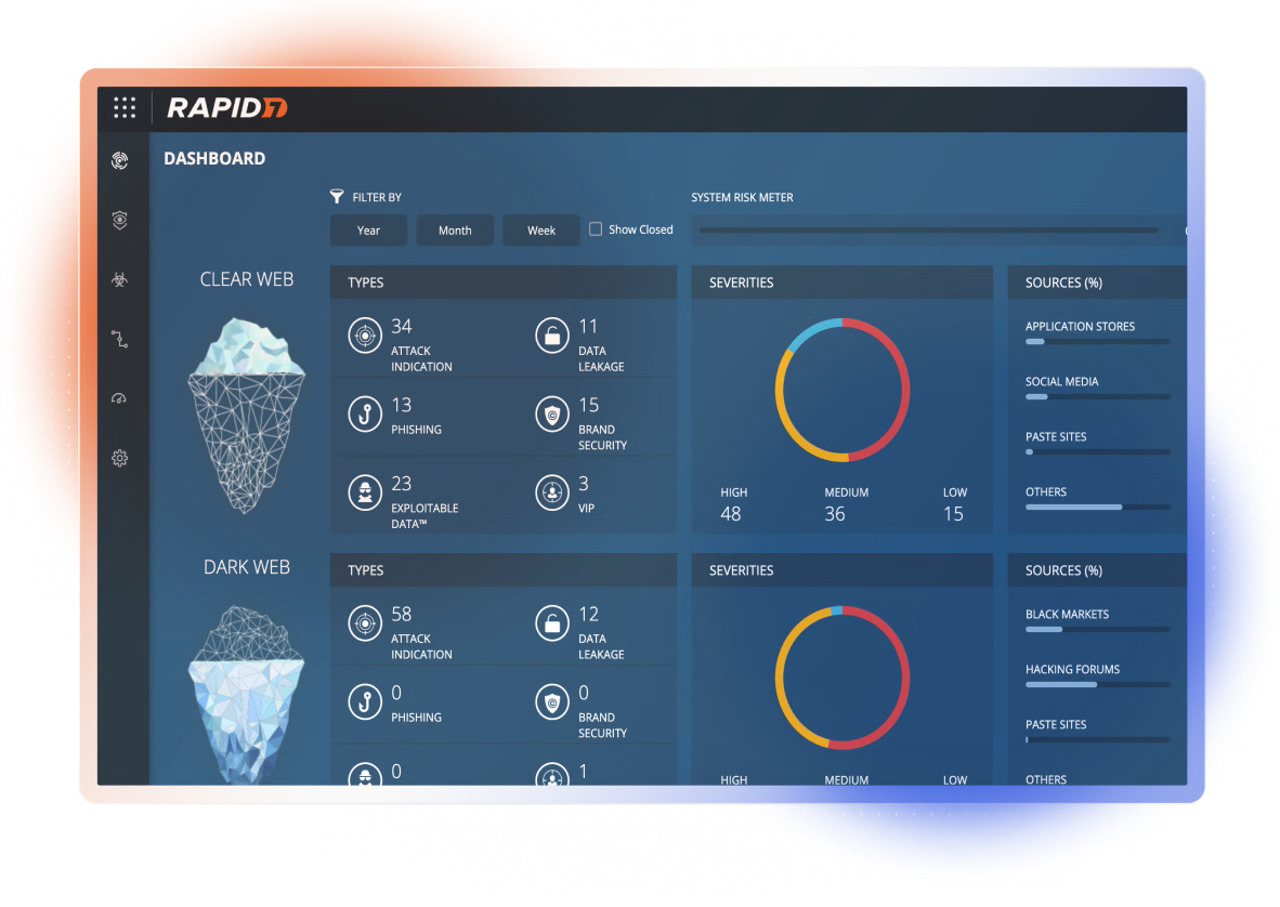
Designed to defend your business from threats emerging across the digital landscape—whether from the clear web, deep web, or dark web. Threat Command keeps you ahead of attackers by continuously monitoring for malicious activity and providing real-time, contextualized alerts. You can proactively investigate malware, phishing campaigns, threat actors, and TTPs.
Threat Protection Expertise
Our team of threat detection experts have spent years building relationships with threat actors, gaining their trust and infiltrating the very same dark forums they use to launch attacks against you. They speak and understand multiple languages, and are available to answer customer questions with a single click right inside the platform.
Rapid Remediation and Takedown
With multi-lingual threat analysts, and a best-in-class takedown rate of 85% in under 24 hours, Threat Command removes the burden of takedown management, enabling organizations to easily take swift action to proactively minimize their digital risk.
Advanced Investigation and Threat Mapping
Dynamic asset mapping framework tracks your evolving digital footprint, identifies new potential attack vectors and understands where you may be exposed. From there you can automatically correlate threat actor intelligence to your unique digital footprint.
Clear, Deep, and Dark Web Protection
Threat Command protects against those bad actors by providing clear visibility into the dark web, so you are always prepared for whatever attackers throw at you. With Threat Command, you’ll get early warning of potential attacks and automated intelligence of vulnerabilities targeting your employees, network, and customers.
IOC Management and Enrichment
Detect and respond faster with a unified view of your digital footprint. Threat Command connects and enriches IOCs in real time, syncing threats, vulnerabilities, and events for automated, prioritized action.
Seamless Automation
Threat Command integrates seamlessly with your entire security stack by automating and monitoring the clear, deep, and dark webs, and drawing on custom research, threat hunting, and external threat feeds to create a clear picture of your entire threat environment.
Expansive Threat Library
Access up-to-date threat intelligence with advanced search and simplified views. Backed by expert analysts, the library includes MITRE ATT&CK IDs, TTPs, and real-world threat data—all in one easy-to-navigate interface.
